 Here's a small sample of popular phishing emails we've seen over the years. As you can see there are many different approaches cybercriminals will take and they are always evolving.
Here's a small sample of popular phishing emails we've seen over the years. As you can see there are many different approaches cybercriminals will take and they are always evolving.
While it would be virtually impossible to keep a current and fully comprehensive archive of these examples, it's a really good idea to keep updated on what's out there to make phishing attacks less likely.
Over the past few years online service providers have been stepping up their security game by messaging customers when they detect unusual or worrisome activity on their users' accounts. Not surprisingly, cybercriminals are using this to their advantage. Many are designed poorly with bad grammar, etc. but others look legitimate enough for someone to click if they weren't paying close attention:
Consider this fake Paypal security notice warning potential marks of "unusual log in activity" on their accounts:
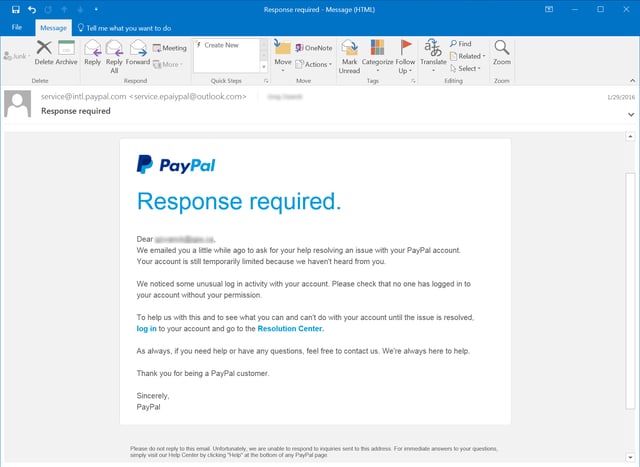
Hovering over the links would be enough to stop you from ending up on a credentials stealing web site.
And here's a fake Microsoft notice, almost identical in appearance to an actual notice from Microsoft concerning "Unusual sign-in activity":
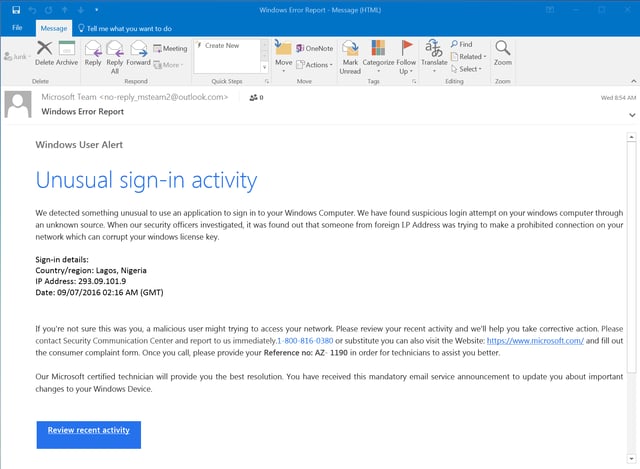
This email points users to a phony 1-800 number instead of kicking users to a credentials phish.
Malicious .HTML attachments aren't seen as often as .JS or .DOC file attachments, but they are desirable for a couple of reasons. First, there is a low chance of antivirus detection since .HTML files are not commonly associated with email-borne attacks. Second, .HTML attachments are commonly used by banks and other financial institutions so people are used to seeing them in their inboxes. Here are a few examples of credential phishes we've seen using this attack vector:
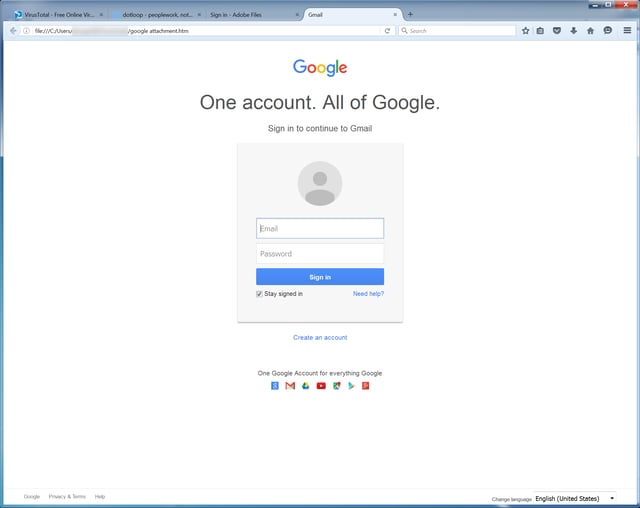
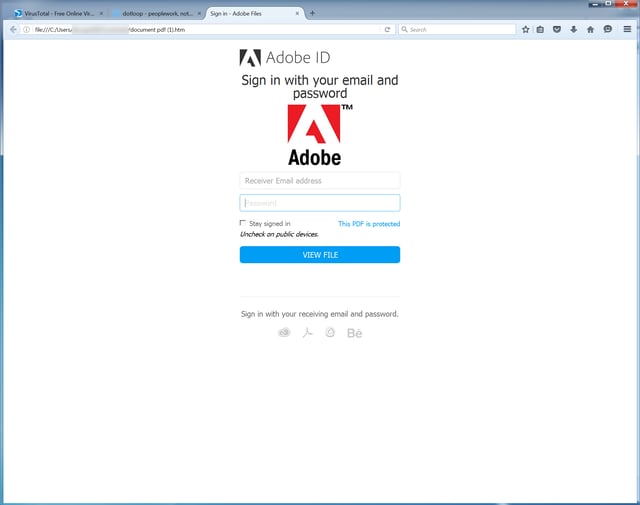
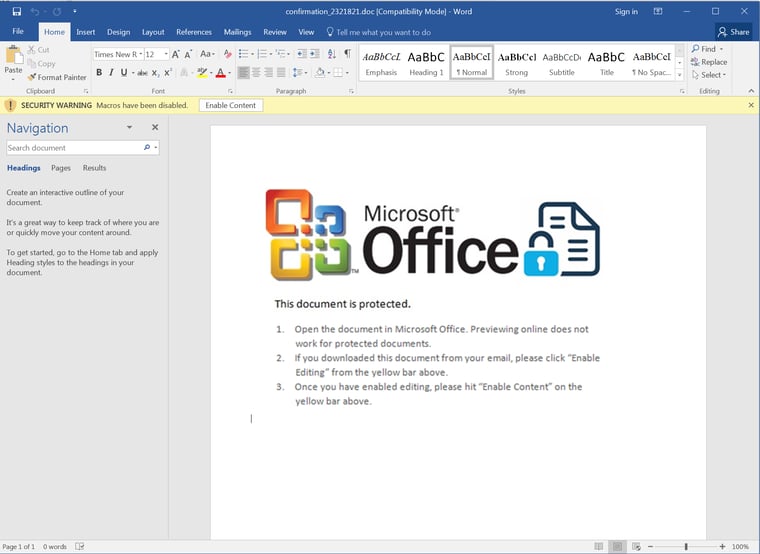
Malicious macros in phishing emails have become an increasingly common way of delivering ransomware in the past year. These documents too often get past anti-virus programs with no problem. The phishing emails contain a sense of urgency for the recipient and as you can see in the below screenshot, the documents step users through the process. If users fail to enable the macros, the attack is unsuccessful.
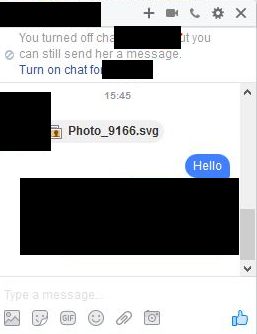
Several Facebook users received messages in their Messenger accounts from other users already familiar to them. The message consisted of a single .SVG (Scaleable Vector Graphic) image file which, notably, bypassed Facebook's file extensions filter. Users who clicked the file to open it were redirected to a spoofed Youtube page that prompted users to install two Chrome extensions allegedly needed to view the (non-existent) video on the page.
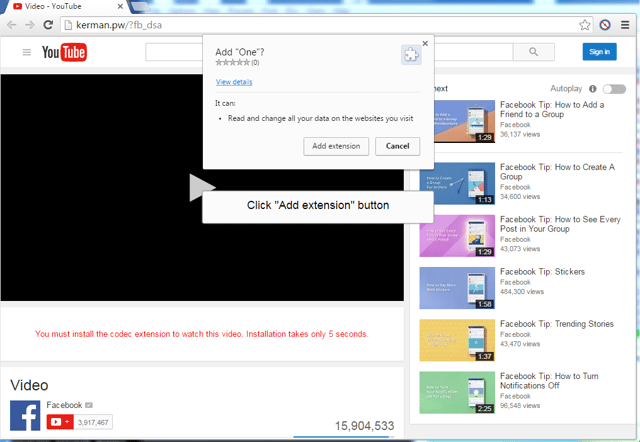
For most users, the two Chrome extensions were used to allow the malware a limited degree of self-propagation by exploiting the "browser's access to your Facebook account in order to secretly message all your Facebook friends with the same SVG image file."
On some users' PCs the embedded Javascript also downloaded and launched Nemucod [PDF], a trojan downloader with a long history of pulling down a wide variety of malicious payloads on compromised PCs. Users unlucky enough to encounter this version of the malicious script saw their PCs being taken hostage by Locky ransomware.
LinkedIn has been the focus of online scams and phishing attacks for a number of years now, primarily because of the wealth of data it offers on employees at corporations. Malicious actors mine that data to identify potential marks for business email compromise attacks, including wire transfer and W-2 social engineering scams, as well as a number of other creative ruses. Here are some examples we've seen through KnowBe4's Phish Alert Button:
In one case a user reported receiving a standard Wells Fargo credentials phish through LinkedIn's InMail: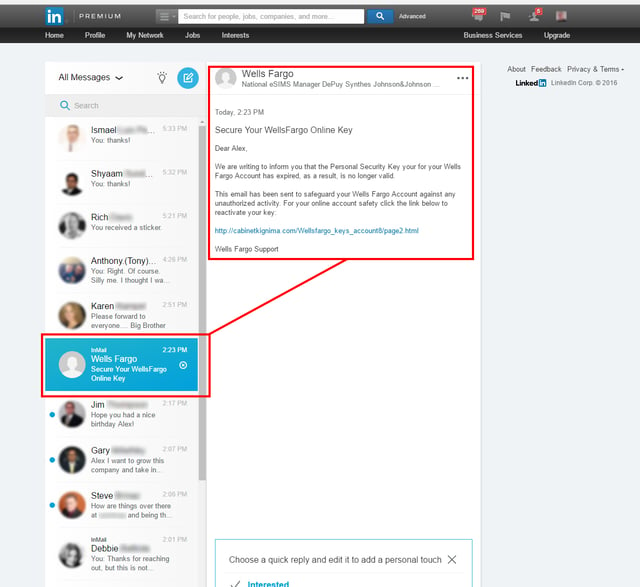
Note that this particular InMail appears to have originated from a fake Wells Fargo account. The supplied link leads to a fairly typical credentials phish (hosted on a malicious domain since taken down):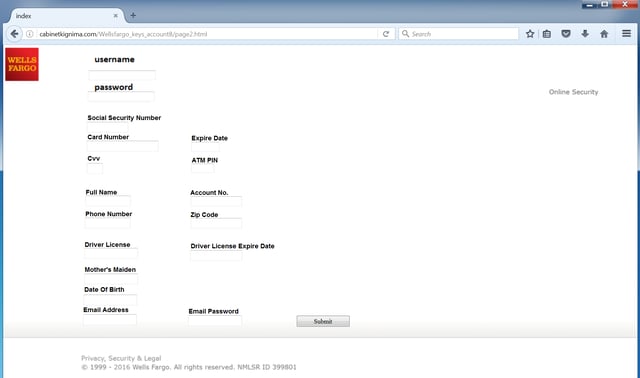
It looks like the bad actors set up a fake Wells Fargo profile in an attempt to appear more authentic.
Another similar phish was delivered to an email account outside of LinkedIn: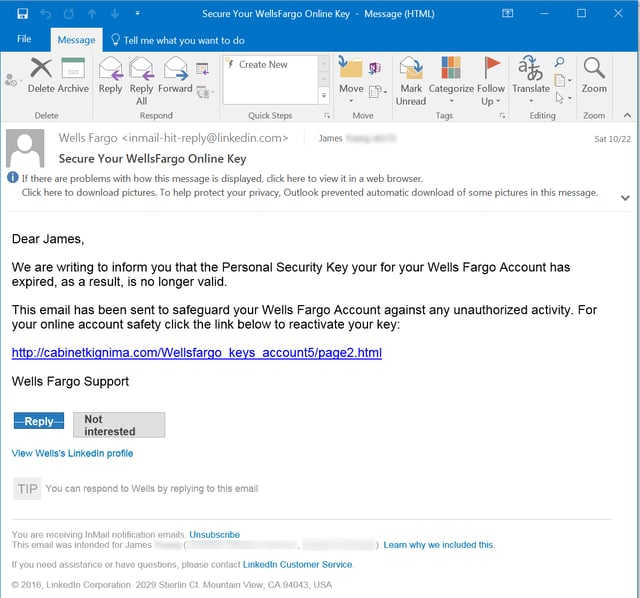
This email was delivered through LinkedIn, as did the URLs used for the several links included in the footer of this email ("Reply," "Not interested," "View Wells's LinkedIn profile"):
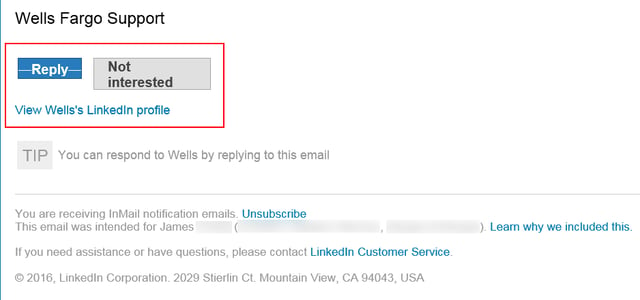
Those URLs were obviously auto-generated by LinkedIn itself when the malicious actors used LinkedIn's messaging features to generate this phish, which hit the external email account of the mark (as opposed to his InMail box, as was the case in the first phish discussed above).
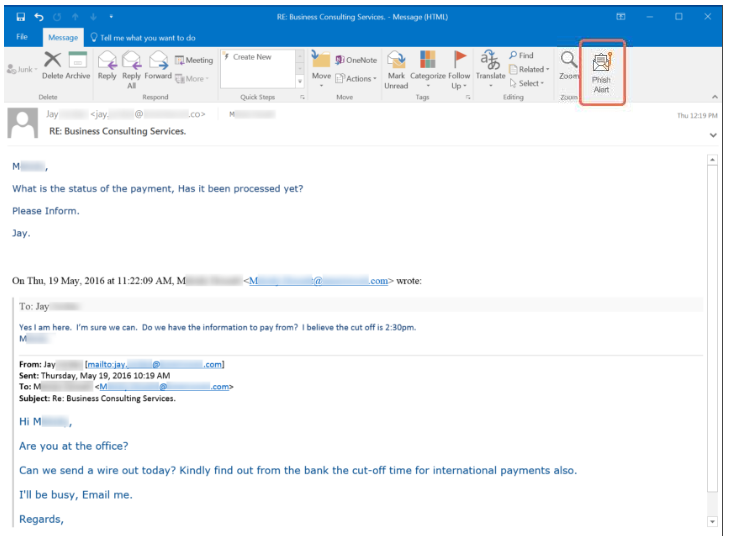
Here's an example of a KnowBe4 customer being a target for CEO fraud. The employee initially responded, then remembered her training and instead reported the email using the Phish Alert Button, alerting her IT department to the fraud attempt.
When the employee failed to proceed with the wire transfer, she got another email from cybercriminals, who probably thought it was payday:
KnowBe4 reports on the top-clicked phishing emails by subject line each quarter which include phishing test results as well as those found 'In the Wild' which are gathered from the millions of users that click on their Phish Alert Button to report real phishing emails and allow our team to analyze the results.
Would your users fall for convincing phishing attacks? Take the first step now and find out before bad actors do. Plus, see how you stack up against your peers with phishing Industry Benchmarks. The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
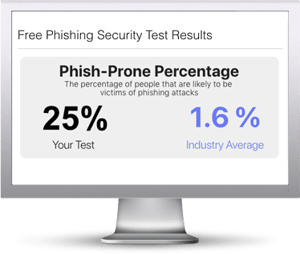 Here's how it works:
Here's how it works:
PS: Don't like to click on redirected buttons? Cut & Paste this link in your browser:
https://www.phishing.org/phishing-security-test
Related Pages: Phishing Techniques, Common Phishing Scams, What Is Phishing
© KnowBe4, Inc. All rights reserved. | Privacy Policy & Terms Of Service